Is Your Financial Future Protected? – Part 3
CYBERCRIME
 Viruses. Trojan horses. Phishing. Malware. The internet is littered with scary-sounding terms that make it seem like shadowy hackers are watching every keystroke and mouse click we make, looking for ways to break into our devices the moment we’re not looking.
Viruses. Trojan horses. Phishing. Malware. The internet is littered with scary-sounding terms that make it seem like shadowy hackers are watching every keystroke and mouse click we make, looking for ways to break into our devices the moment we’re not looking.- Fail to recognize basic scams and fraud, many of which are old as time and have been merely adapted to the digital age.
- Fail to keep our “digital doors locked” when using our computer or mobile devices.
- Engage in unsafe practices or visit insecure websites — the virtual equivalent of finding yourself in the “wrong part of town.”
COMMON FORMS OF CYBERCRIME
Your computer as a target…
The term is MALWARE, which is a portmanteau for MALICIOUS SOFTWARE. Think viruses, worms, Trojan horses, etc. Malware is the classic example of a cybercrime, in which your computer is the primary target rather than your identity or your bank account (although these may be indirect targets, and the lines between the two are becoming increasingly blurred). Malware has been around for decades, but it was the rise of the internet that made it the preferred toolkit for a new generation of thieves. Here are six of the most common types.
 |
Computer VIRUSES – A virus is a type of program that replicates itself by modifying other programs and inserting its own code. One of the oldest types of malware, viruses are less common than they used to be since antivirus software has become more effective. But they still cause billions of dollars’ worth of economic damage each year, and can corrupt your data, slow down your devices, or even cause a complete system failure. As a result, dealing with viruses can be very expensive. How you get them: Email attachments, internet downloads. |
 |
Trojan horses – A Trojan horse is a malicious program that looks normal, benign, or even helpful, in order to convince the user to install it. But once installed, Trojans can give hackers backdoor access to your computer, enabling them to steal information, spy on you, install more malware, and more. How you get them: Internet downloads. |
 |
Worms – Worms are an extremely common form of malware. These spread over computer networks like the ones in offices, college campuses, or other institutions. Unlike viruses, they don’t require any user action to replicate. Some worms do little damage while others can give hackers access to your system, similar to Trojans. All worms, however, can spread very easily. How you get them: Email attachments, visiting bad websites, running out-of-date software. |
 |
Spyware – Spyware tracks your internet activity: browsing habits, Google searches, login information, even your keystrokes! While it may sometimes be just an annoyance, it can also represent a serious threat to your privacy and the security of your bank account. How you get it: Spyware often comes from Trojans but can also be bundled with legitimate software. |
 |
Adware – Adware is software that persistently and aggressively puts unwanted advertisements on your computer screen, often in the form of a “pop-up” or browser window that can’t be closed. It can redirect you to advertising websites, change your internet browser settings, search settings, homepage, and more. Most ominously, adware can also collect your data. Some of the newest forms of adware can even disable your anti- malware protection. How you get it: Using an out-of-date browser, clicking on certain ads or visiting disreputable websites. |
 |
Ransomware – Ransomware tends to dominate the news, and for good reason: It can hold entire corporations’ hostage. It’s a type of malware that essentially locks you out of your data, or even your device, until you pay the ransom. Sometimes it’s merely a scam designed to trick you, and sometimes it’s not. How you get it: Ransomware is often installed on your device via Trojans or worms. Like most other forms of malware, the main culprit is opening unexpected emails and attachments. |
Your computer as a tool…
Rather than a target in and of itself, more and more thieves are seeing your computer and other devices as a tool to target you. These types of crimes don’t require as much technical expertise and range from sophisticated to crude. In fact, most of the crimes in this category have been around for centuries. The internet simply represents a new and more dangerous tool for them to use against their victims.
The main crime we will discuss here is known as PHISHING.
 Phishing
Phishing
Imagine this scenario. You get an email that appears to be from your bank. You open it and read a message that either looks extremely convincing, or is riddled with misspelled words. Either way, you are directed to “click the link below.” You click the link, and are taken to a page that looks almost exactly like the website you’re used to visiting.
Almost.
You’ve been phished.
Hopefully, this scenario has never happened to you. Or if it has, you recognized the warning signs and knew to stay away. Unfortunately, many people don’t recognize those warning signs, and so fall prey to a particularly insidious form of internet fraud called phishing.
Phishing is when hackers and cyber-thieves try to trick people into submitting their personal information by creating fake versions of existing websites and/or sending emails and text messages that look like they are coming from a legitimate bank, business, or government agency. Sometimes, phishing can even take place over the phone!
A play on the word “fishing” (with regular people as the prey and the fake message/website as the bait), the crooks behind phishing try to dupe people into giving out sensitive information, like their Social Security numbers, account passwords, credit card numbers, or even bank PIN numbers.
Often, victims of phishing are directed to websites that automatically install malicious software onto their computer or mobile device. Either way, phishing poses a major threat to your finances, your identity, or your data.
Thankfully, phishing is easy to avoid if you follow a few common-sense rules:
- Legitimate banks, retailers, and agencies will never ask for your personal information via email. If you receive a message from someone asking for this, assume it’s a scam.
- Furthermore, as a rule of thumb, do not reply to any message, electronic or otherwise, that requests your personal information.
- Never use links in an email to connect to a Web site unless it’s an email you expected from a source you KNOW is trustworthy. Instead, open a new browser window and type the site address in directly.
- Always double-check the URL of any site you intend to visit. Some thieves set up sites with URLs that look very similar to a legitimate site. For example, “amzon.com” instead of “amazon”, or “facebok.com” instead of “facebook.” You get the idea.
- When doing business online, look at each website’s address. Secure websites should have a small symbol of a lock next to their URL, or the letters https (instead of merely http) at the beginning of the address. Both indicate that the site has been verified as secure.
WHO IS MOST VULNERABLE
WHO IS MOST VULNERABLE – By state
Anyone who uses the internet is potentially vulnerable to cybercrime or data breach. But just as with identity theft, some states seem to be particularly at risk. Here are the top ten, based on FBI data and the National Governor’s Association.
.
- HAWAII
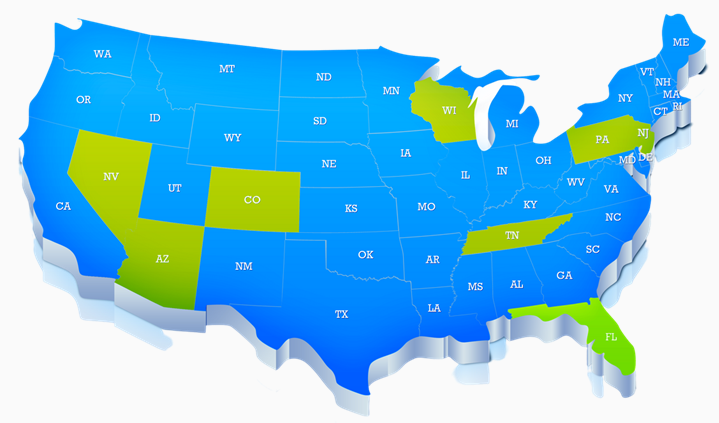
- PENNSYLVANIA
- NEVADA
- FLORIDA
- WISCONSIN
- ARIZONA
- NEW JERSEY
- ALASKA
- COLORADO
- TENNESSEE
SOURCE: Security.org
RECOGNIZE WHAT COMMON PHISHING MESSAGES LOOK LIKE
Some phishing messages may be extremely sophisticated and be virtually indistinguishable from the real thing at a glance. But there are often some telltale signs, and most phishing messages tend to be crude if you pay attention.
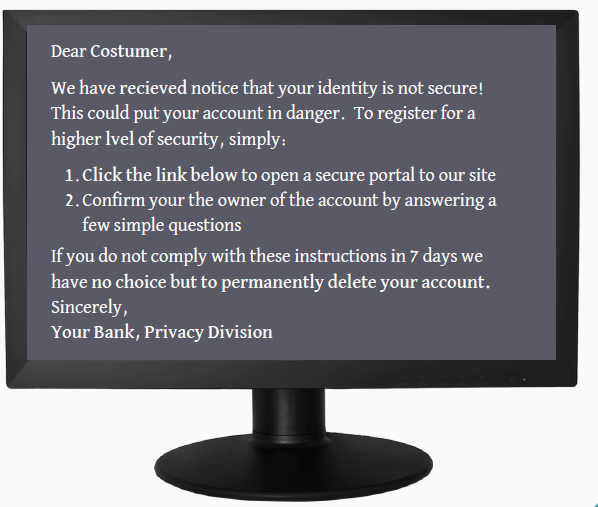
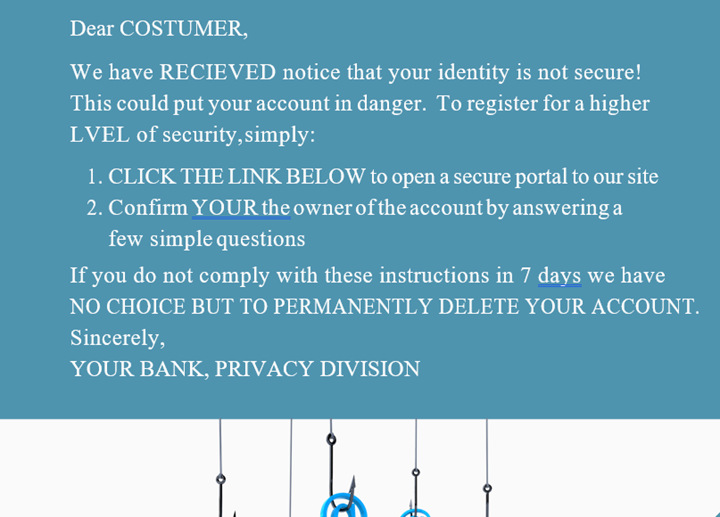
The warning signs in this email — a real phishing attempt that was caught — aren’t hard to spot. Notice the misspelled words? (Costumer, recieved, lvel.) The link to click on? Or what about the threat? (“If you do not comply…”) And of course, there’s the reference to your bank or some other well-known organizations.
Here is the message again. Spot the red flags?
STEPS TO PROTECT YOURSELF FROM PHISHING
 |
REMEMBER THIS: Legitimate banks, retailers, agencies, and institutions should never ask for your personal information — like passwords, PINs, and Social Security Numbers – via email. If you receive a message from anyone asking for this info, assume it’s a scam. Furthermore, as a general rule, don’t reply to any message, electronic or otherwise, that requests your personal information. |
 |
DON’T DO THIS: Don’t click on a link in an email to connect to a website unless it’s from a source you know is real and trustworthy, like a family member. Instead, hover your mouse over the link to verify the address, or search for the site on Google. And NEVER click on an attachment you’re not expecting! The same is true for any links you see on social media, like Facebook. |
 |
ALWAYS DO THIS: Always double-check the URL of any site you intend to visit. Some times set up sites with URLs that look very similar to real sites. For example, “amzon.com” instead of “amazon” or “facebok.com” instead of “facebook.” Also, check to see if sites have a symbol of a lock next to their URL, or begin with the letters https (instead of merely http). Both indicate the site has been verified as secure. |
 |
WATCH OUT FOR THIS: Phishing emails and websites may look legitimate at first glance, but the warning signs often stick out upon closer inspection. In particular, watch out for misspelled words, broken English, and threats. Variations on “If you don’t comply” is a common phrase. |
CYBERCRIME PROTECTION CHECKLIST
Now that you know a little more about cybercrime, here are some simple — but crucial — steps to keeping yourself and your finances “cyber-secure”.
1. Keep all of your software up to date.
What does this have to do with cybersecurity? Everything. You see, one of the easiest targets for hackers to attack is outdated software. That’s because older applications often contain weaknesses that hackers can use to gain access to your devices. Your web browser — Chrome, Firefox, or Safari, for example — can be especially susceptible. That’s why you should always:
-
- Turn on automatic system updates for your computer, tablet, or smartphone.
- Download updates and software patches when prompted.
- Frequently review the apps on your devices. Remove the ones you don’t need and update the ones you do.
- Familiarize yourself with your browser’s extensions.(For example, Flash, Java, AdBlocker, etc.) Keep these updated, too.
2. Use stronger passwords via a password management tool.
Your email. Your bank. Your Facebook account. These days, we all have to juggle dozens of passwords. There’s no way to memorize them all, so many people resort to using the same two or three passwords for everything. To make matters worse, these passwords are often extremely simple. (Please don’t be the person who uses “1234” or “password” as their password.)
As a rule of thumb, your passwords should always:
-
- Contain at least eight characters.
- Contain at least one uppercase letter, one lowercase letter, one number, and several symbols. (Symbols include exclamation points, question marks, and asterisks.)
- Be different from one another. Don’t use the same password twice.
- Change at least once per year.
To help with this, consider downloading a password management app. These are handy tools that make managing passwords a breeze. With a password manager, you only need to memorize one password — for the manager itself — instead of dozens. The app will do the rest, automatically inserting the right password whenever you need it. Popular password managers include LastPass, Dashlane, 1Password, and Bitwarden.
3. Embrace two-factor authentication.
Two-factor authentication is a technical term for a simple concept. Think about the front door of your home. It probably has two locks – a handle lock and a deadbolt. While the deadbolt is a second layer of security for your home, two-factor authentication is a second layer of security for your identity.
Normally, when you log into an app or website, you type in your username and password. Two-factor authentication goes a step further by requiring you to enter at least one additional form of authentication. This is often a personal identification number, like a four-digit code. It can also be a second password, the answer to a question only you would know, or even your fingerprint. Only by entering two different forms of authentication can you login to the app or website.
Yes, two-factor authentication adds another five seconds to the process. But it also makes it much harder for thieves and hackers to access your email, Facebook profile, or Amazon account. Use it!
4. Use antivirus (AV) protection software.
Back to basics here. It’s been around for decades, but good AV software is still critical to protecting yourself from viruses and malware. Be advised, though, that it’s better to use one program than two or three. Multiple AV programs can clash with each other, slowing your device and paradoxically leaving you more open to attack. So, rely on one good program you can trust, and remember to keep it updated!
5. Backup your data regularly.
Backing up your data will make your life much easier if you do become a victim of malware. Oftentimes, restoring your data via backup is the only way to return your device to normal.
Keep three copies of your data. One can be kept on your local hard drive. The second should be kept on an external hard drive. The third should be kept in the cloud. Google Drive, Microsoft OneDrive, Apple iCloud, and Dropbox are four popular examples of cloud storage.
6. When in doubt, keep out.
In the outside world, it’s usually healthier to be positive than cynical. But the internet is not the outside world. It’s the Wild West. A little cynicism or skepticism can go a long way toward keeping you safe. So:
-
- If you aren’t sure an email is legit, don’t read it.
- If you weren’t expecting an attachment, don’t open it.
- If you weren’t purposefully shopping online, ignore any and all ads you didn’t search for.
- If you’re not sure where a link goes, don’t click on it. If you feel uncertain about a website, don’t visit it.
- If you’re ever asked to do or share something that you’re not comfortable with, SAY NO!
Remember, you can always open that email, visit that website, or click that link later after you verify it’s real. But undoing something you wish you hadn’t done? That’s a lot harder. So, when it comes to keeping your device, your data, your finances, and yourself cyber-secure…
WHEN IN DOUBT, KEEP OUT!
TIMES TO BE ESPECIALLY WARY
While financial security should be a priority 365 days a year, there are certain times when people are more susceptible to fraud and identity theft. Here are three times you should be particularly vigilant:
Around the Holidays…
 The holiday season — Christmas especially — is a magical time of year. But it’s also a stressful one. Because people have so many things to do, they often fail to pay attention to the warning signs we discussed earlier. Thieves know that, and act accordingly.
The holiday season — Christmas especially — is a magical time of year. But it’s also a stressful one. Because people have so many things to do, they often fail to pay attention to the warning signs we discussed earlier. Thieves know that, and act accordingly.
Here are some potential scams you may encounter around the holidays:
Phishing Scams
During the holiday season, the twist on this scam may include thieves posing as shipping companies or online retailers, asking for personal information to resolve a shipping error.
Their goal is to get personal information from people who are worried their online purchases won’t ship in time for Christmas. Another holiday flavor to this scam is individuals posing as a legitimate organization asking for charitable donations, hoping to capitalize on your holiday generosity.
 Gift Card Scams
Gift Card Scams
With this scam, thieves will go into retailers and find gift cards that are yet to be purchased. They write down the numbers to the gift cards and track them electronically until they are purchased. Once activated upon purchase, the scammer will drain the funds leaving the gift card empty for its rightful owner. To avoid this scam, avoid purchasing gift cards that are either damaged or do not have packaging.
If you feel uncomfortable buying a gift card you find in a store, you can always ask the staff if they have any in the back that haven’t been accessible to the public. Also, to further protect yourself, avoid buying gift cards from third party vendors you aren’t familiar with.
Fake Coupons
With everyone trying to save a little money on their Christmas shopping, coupons can be a handy resource. Unfortunately, there are scammers who set up websites that provide fake coupons in order to steal personal information. Be wary of websites offering coupons or discounts to third parties in exchange for personal information.
Counterfeit Gifts
Just as everyone is trying to save money with coupons, people are also on the hunt for deep discounts. Another scam to avoid this year is the sale of counterfeit goods. If this year’s newest smartphone or gadget is being sold for a price that seems too good to be true, it probably is! To avoid this type of scam, do your research on how to identify authentic goods, or purchase these items directly from the manufacturers.
Tax Season…
 Tax season is another stressful time. With so many people desperate to get their filing done in time, swindlers and con artists know this is the perfect time to go after your identity. Don’t let them! Here are some common tax-season scams.
Tax season is another stressful time. With so many people desperate to get their filing done in time, swindlers and con artists know this is the perfect time to go after your identity. Don’t let them! Here are some common tax-season scams.
Phishing Scams
Yep — phishing again! During tax season, watch out for emails purportedly from the IRS promising a refund or threatening some sort of penalty or legal action against you. They’re all bogus! The IRS will never contact you by email, text message, or social media to request any personal or financial information from you.
Phishing by Phone
This is similar to the scam above, except it’s by phone. If you get a call from someone claiming to be an IRS agent who is making threatening calls demanding money, hang up. Same if you get a call asking you to “verify your information.” Instead, if the IRS needs to get in touch with you, they’ll usually do it via the regular mail.
Refund Scams
Watch out for people who promise a bigger-than-usual refund if you’ll only let them prepare your taxes — all you have to do is sign a blank check or allow them to take a percentage of your refund. Legitimate tax preparers should never ask for these things. Nor should they make outlandish promises before they even look at your tax situation. Often, these are scammers who will try to file a false return in your name so they can claim your refund for themselves.
During a Crisis…
Scams often go up whenever there is a crisis. Sometimes the crisis could be a natural disaster, like after an earthquake or hurricane. Or it could be a health crisis. During the coronavirus pandemic, for example, data breaches and online scams went up dramatically. The same was true during the 2008 financial crisis. Again, phishing is the method of choice. Thieves will often pose as government officials, either via email, text messages, or even robo-calls, requesting your personal information in order to qualify you for government assistance. Given that the government often does provide some sort of assistance during a crisis, these scams can often seem very convincing.
In addition to the steps you’ve already learned, the best thing you can do to protect yourself is to simply stay informed about what the government is and is not doing to help during a crisis. While the media — like almost everything else — has become a contentious political topic in recent years, the fact remains that national news outlets, or your local news organizations, are simply more reliable than any email, text message, robo-call, or post on social media when it comes to this sort of thing.
WHAT TO DO NEXT
Take a few minutes to think about everything you just read. Think about your long-term goals and your short-term needs. Has anything changed? Does anything need to change? Are you as prepared as you should be?
If you feel it’s time to become more “financially secure”, then let’s talk. We can meet over the phone or online to determine what areas need to be addressed. If you need expert help on any of these topics, I can also put you in touch with professionals I know and trust.
In the meantime, I hope you found this information to be interesting and helpful. As always, please let me know if there is ever anything I can do for you.
Above all,
remember to be vigilant.
Be careful.
Be financially cybersecure.
#2ndHalfWealth 1-05054319 03/31/2022
Disclaimer: Content in this material is for general information only and not intended to provide specific advice or recommendations for any individual.
Sources: This material was prepared by Greg Young and Bill Good Marketing